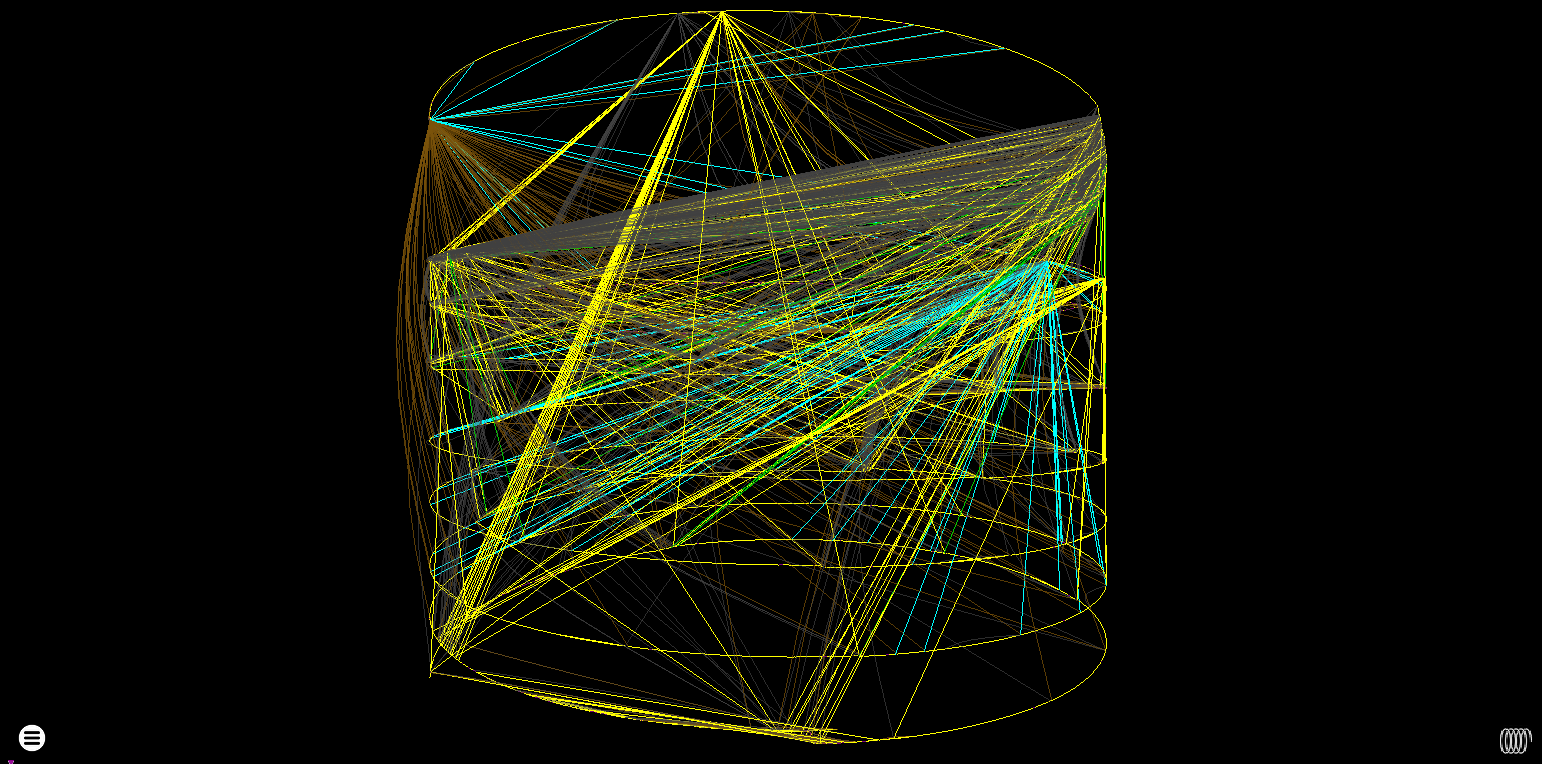
Instruction Trace Visualisation: Packers & Protectors
Software protectors can be a bit of a trial by fire for binary analysis tools - this post shows some visualisations of a few packers and protectors often used for malware. It’s intended to be a record for how rgat’s visualisation capabilities evolve - so expect the first entry to be a bit rough.
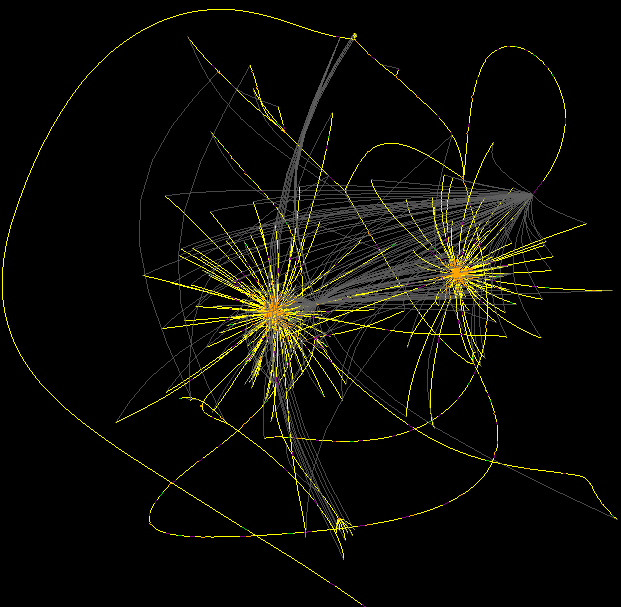
The Eldritch Birds Nest - Control Flow Graph Clumping
Modern compilers generate a lot of code that gets poor results from force-directed graph layouts. This post discusses why and some steps being taken to improve it.
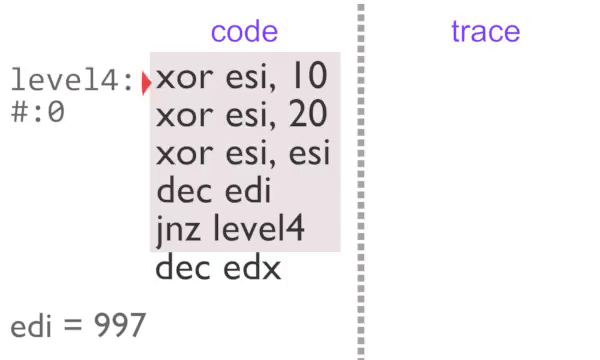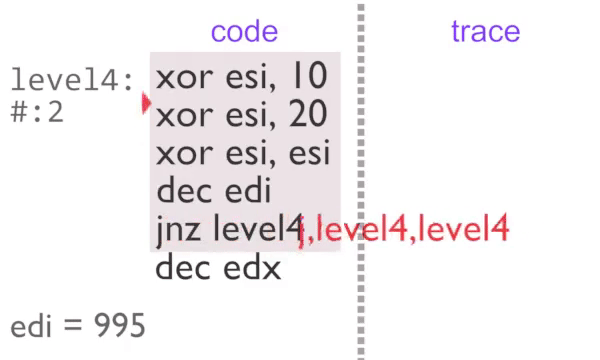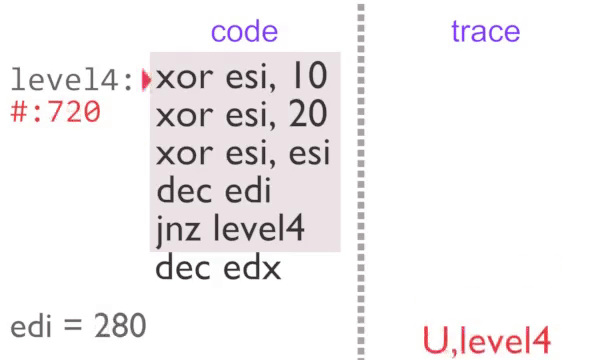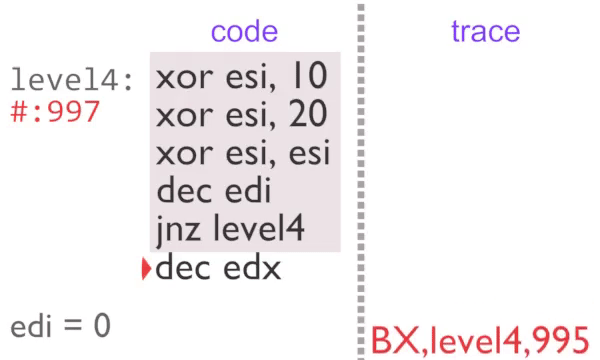
Recording Large Instruction Traces - Quickly
rgat operates by reading instruction traces, converting those to a graph and then laying those graphs out into plots. The problem here is that computers can generally execute instructions faster than they can record, analyse and make fancy graphs with them.
